Radio Frequency 101: Can You Really Hack a Radio Signal?
PUBLISHED IN
Cyber-Physical SystemsIn 2017, a malicious actor exploited the signals in Dallas’s emergency siren system and set off alarms for over 90 minutes. These types of attacks can affect devices that use radio frequency (RF) technology, from smart security systems to aircraft. RF also plays a critical role in many military systems such as navigation, radar, and communication systems. Common DoD use cases include satellite communication (SATCOM), radar, and tactical data links that help coordinate troop movements, signal position information about a target, or help maintain communication between aircraft and drones. A recent report indicated the DoD is susceptible to potential RF attack vectors, indicating the need to better understand and prevent vulnerabilities.
In this RF 101 guide, we explore some of the fundamentals of radio frequency communication, delve into the generalities of protocols and device interactions, discuss common RF tools, and uncover ways malicious actors can attack systems. We summarize the basics of RF technology and the risks associated with it, and we discuss how the SEI is helping to secure wireless communications.
RF Fundamentals
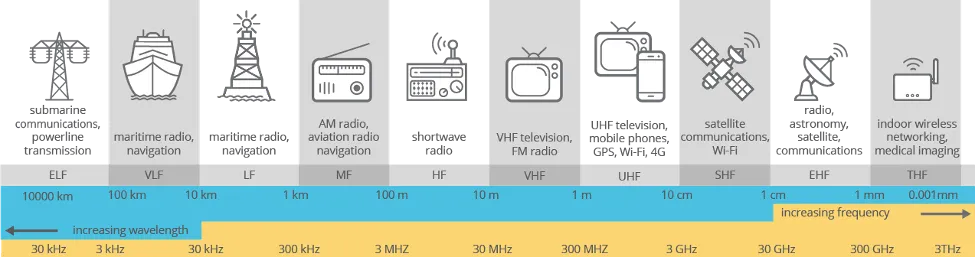
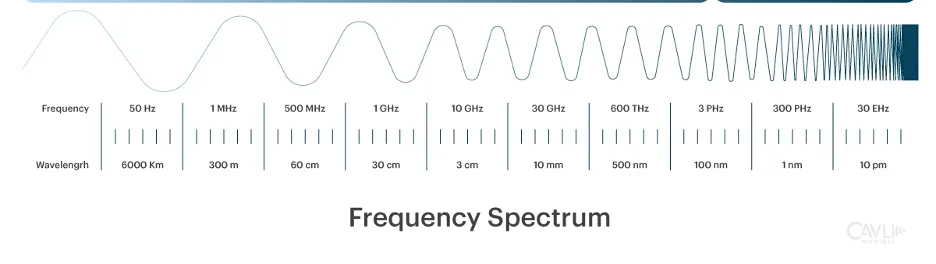
The electromagnetic spectrum covers the entire range of electromagnetic waves from very long radio waves to visible light to very short, high-energy radiation such as X-rays and gamma rays. The radio spectrum is a subset of the broader electromagnetic spectrum and ranges in frequency from 3 Hz to 3,000 GHz. The ability of RF waves to propagate, or travel through different mediums, including the vacuum of space, enables wireless communication without the need for physical connection. RF signals are fundamental to modern communication systems, which enable many of today’s technologies including television, radio broadcasts, cellular communication, and Wi-Fi connections. Wireless RF communication also plays a vital role in space domains, such as satellite communication to ground stations, which enable transmission of telemetry data, GPS, and other signals. The radio spectrum can be divided into standardized bands ranging from extremely low frequency (ELF) to tremendously high frequency (THF) as seen below.
What Are Protocols and RF Modules?
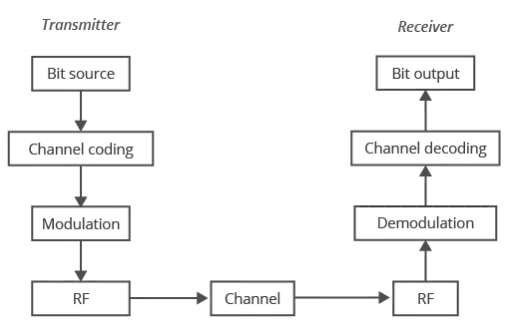
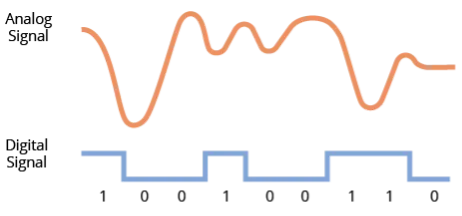
RF modules are small electronic devices that are used to transmit and receive radio signals between two devices that are physically separated. Transmitters are responsible for transmitting radio waves that carry analog or digital information, and receivers receive the radio waves and recover the information. This is the concept of a wireless communications channel, the open-space path through which information is transmitted via electromagnetic waves without the use of physical connections such as wires or cables. The overall signal is constructed of the carrier signal, a periodic waveform that conveys information via modulations that encode the analog or digital information. Modulation is the process of varying a carrier signal to encode data then demodulating that received signal to decode data. Modulation techniques determine how information is transmitted over radio waves, affecting the efficiency and quality of communication.
There are different ways that the information can be modulated. Common analog modulations include amplitude modulation (AM) and frequency modulation (FM). AM modulates a higher frequency carrier with a lower frequency signal by adjusting the amplitude of the carrier signal. The frequency of the carrier is unaltered, but the amplitude varies constantly. FM modulates by making relatively small adjustments to the frequency of the carrier. These two methods characterize the kinds of RF signals on the familiar AM and FM radio bands. Common digital modulations, building on AM and FM, include amplitude shift keying (ASK) and frequency shift keying (FSK).
Within a system, transmitters and receivers can be packaged together as transceivers, which perform both functions. Additionally, system on a chip (SoC) configurations integrate microcontrollers with the transceiver to allow protocol management such as data packetization.
Communication protocols are sets of rules for the exchange of information between the transmitter and receiver. They ensure data is transmitted in a consistent format, allowing devices from different manufacturers to communicate efficiently if they respect the protocol. There are many different kinds of protocols in use. The most instantly recognizable communication protocol for many is cellular wireless.
Cellular wireless is the commercial driver of the digital wireless communication revolution. From its commercial introduction more than 30 years ago for mobile voice communication, digital wireless technology has evolved, extending the internet to our mobile devices. At a glance:
- 1.22 billion cell phones were produced in 2024.
- There were more than 8.58 billion mobile subscriptions in use worldwide in 2022, compared to a global population of 7.95 billion.
- The latest data reveal that 70.7 percent of the world’s total population now uses a mobile phone.
- A staggering 59 percent of Kenya’s GDP flows through M-PESA, the country’s dominant mobile payment system. A growing number of countries are adopting similar e-commerce models.
The continued evolution of the world-wide cellular data network is driven by two organizations filling distinct but interconnected roles. The International Telecommunication Union (ITU), sets the overall requirements and guidelines for international mobile telecommunications (IMT) standards. The 3rd Generation partnership Project (3GPP), a global collaboration of commercial, standards, and other interested organizations, performs studies and then develops technical specifications for mobile communication technologies. The ITU guides, reviews, and approves 3GPP's specifications as international standards, ensuring they meet global requirements.
The 3GPP parallel study and specification process has maintained a cadence of a specification release every one to two years since 1990. These include packet-switched data, which provides “always on” connection, eliminating dial up and improving access to email and web services. LTE Release 8 implemented an adaptation using QPSK, 16QAM, and 64QAM modulation. Later releases included additional modulations. A timeline of commercially recognizable releases is presented in the table below:
| Year | Release | Name | Features | Modulation / Access | Downlink Data Rate (bits/sec) |
| 1992 | Phase1 | 2G / GSM | GSM Commercially Offered DCS-1800 | GMSK/TDMA | 9.6 k |
| 1997 | 96 | 2G / GSM | Circuit Switched User Data | GMSK/TDMA | 14.4 k |
| 1998 | 97 | 2.5G / GPRS | Packet Switched User Data | GMSK/TDMA | 56-114k |
| 1999 | 98 | 2.75G / EDGE | Enhanced GPRS | 8PSK/TDMA | 384 k (max) |
| 2000 | 99 | 3G / UMTS | W-CDMA Interface | QPSK/W-CDMA | 384 k |
| 2002 | 5 | 3G / UMTS | HSDPA | 16QAM/W-CDMA | 2-12 M |
| 2008 | 8 | 4G / LTE | LTE Introduced | OFDMA | 5-100M |
| 2018 | 15 | 5G / NR | NR Introduced | OFDMA | 100-1000M |
Some additional frequently used wireless protocols include:
- Wi-Fi: This is the familiar wireless IEEE 802.11-based protocol that operates in the 2.4 GHz ISM Band with 14 channels spaced 5 MHz apart. In the United States, channels 1 through 11 are commonly used, especially channels 1, 6 and 11, which are the only non-overlapping channels. Wi-Fi is used in homes, city infrastructures, geolocation, industrial environments, and Internet of Things (IoT) applications.
- Bluetooth low energy: This is the familiar low-power protocol used by diverse devices for close-proximity communication. It operates in the 2.4 GHz ISM Band. Frequency-hopping spread spectrum (FHSS) is the modulation technique used, and its band is divided into 40 2-MHz channels. It is used in smart home devices, healthcare applications, location-based services, and more.
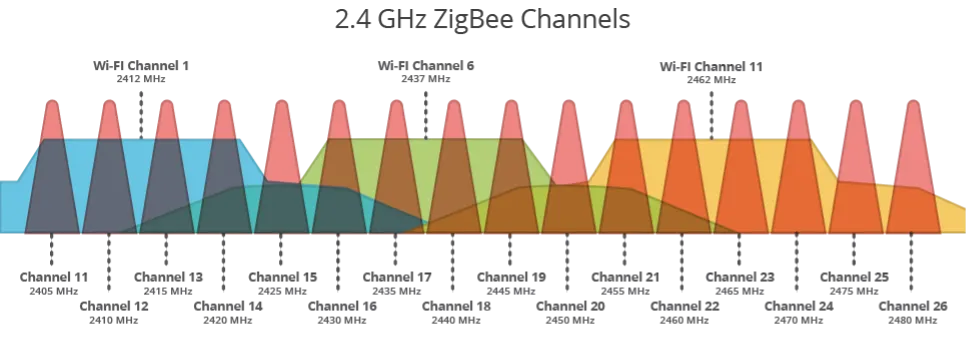
- Zigbee: This low-power wireless mesh network protocol is under the IEEE 802.15.4 radio specification. It operates on the 868 MHz radio band in Europe, the 915 MHz radio band in North America and Australia, and globally at 2.4 GHz. It can transmit over a distance of up to 100 meters (line of sight) and can achieve raw data throughput rates up to 500 kbps. Zigbee operates on 16 fixed channels that are 5 MHz apart in the 2.4 GHz band. It is mainly used in home automation, smart energy, wireless sensing and industrial automation.
How Do Devices Communicate with One Another?
Devices communicate by encoding data into modulated signals on a carrier wave at a specific frequency. As seen in Figure 5, two Zigbee radios communicating on channel 19 would be communicating at the frequency of 2445 MHz.
Antennas are required in wireless communication since they are responsible for radiating signals into the air (i.e., transmitter) and receiving the incoming signals (i.e., receiver). Antenna designs are determined by the nature of the communication application, the intended frequencies and modulation method, and quality factors such as range, bandwidth, and operating environment.
Multiplexing is a method that allows multiple transmitted signals or streams of information to be shared over a single shared communication channel. Frequency division multiplexing allows multiple users to send data through a single communication channel by dividing the total channel into multiple sub-channels with non-overlapping carrier frequencies. These sub-channels are allocated to separate users or devices. For example, Zigbee, as noted above, operates on 16 channels in the 2.4 GHz range. Time division multiplexing schemes help manage access to a channel by allocating individual users or devices a specific timeslot for information transfers on the same shared carrier frequency to avoid colliding transmissions. Users or devices transmit in rapid succession, each with their own timeslot. There are also more complex approaches to multiplexing such as code division multiplexing which use advanced techniques like direct sequence spread spectrum or frequency-hopping spread spectrum to allow users access to the entire bandwidth for the entire duration of transmission by assigning each device/user a unique, orthogonal code.
RF Attacks
RF attacks exploit vulnerabilities to intercept, disrupt, or manipulate systems and associated protocols. The consequences of RF attacks can range from data breaches and loss of confidentiality to denial of service and disruption of critical communications. An example that illustrates RF security risks is railroad and train jacking, as in the recent Poland railway attack stopped 20 trains in 2023. As wireless technology grows, so do the attack field and threats.
What Are Common Types of RF Attacks?
Several common RF attack vectors exploit weaknesses in wireless communications. Common vectors include the following:
- Eavesdropping involves intercepting and listening to wireless communications without authorization. This can allow a malicious actor to gain access to sensitive information such as passwords, authentication processes, personal information, or import system processes. Attackers can utilize software-defined radios (SDRs) to capture and decode transmitted data in a flexible manner, enabling attackers to rapidly adapt as they learn more about frequencies, modulation techniques, and protocols.
- Replay attacks, which are analogous to man-in-the-middle (MITM) attacks in cybersecurity, occur when an attacker captures valid transmissions and then retransmits them to impersonate a legitimate device or user. These attacks can bypass authentication or gain unauthorized access to systems. For example, a malicious actor could sniff the transmissions that carry the code from a smart lock to unlock/lock a door or sniff and replay the rolling code from a vehicle's key fob to obtain entrance to a car.
- Relay attacks enhance a valid radio signal and use it to access a valid target. Unlike a replay attack, which captures and resends the signal, a relay attack allows a signal to travel farther and be used at longer distances. Smart fobs and keys are susceptible to this type of attack.
- Jamming is a denial-of-service attack where the attacker transmits radio signals on the same frequency as the targeted communication, effectively disrupting or blocking the legitimate signals. This can prevent devices from communicating, which can lead to service outages or operational disruptions.
RF Vulnerabilities
In this section, we analyze recent examples of notable RF attacks that have been written about in the public press.
Replay Attack
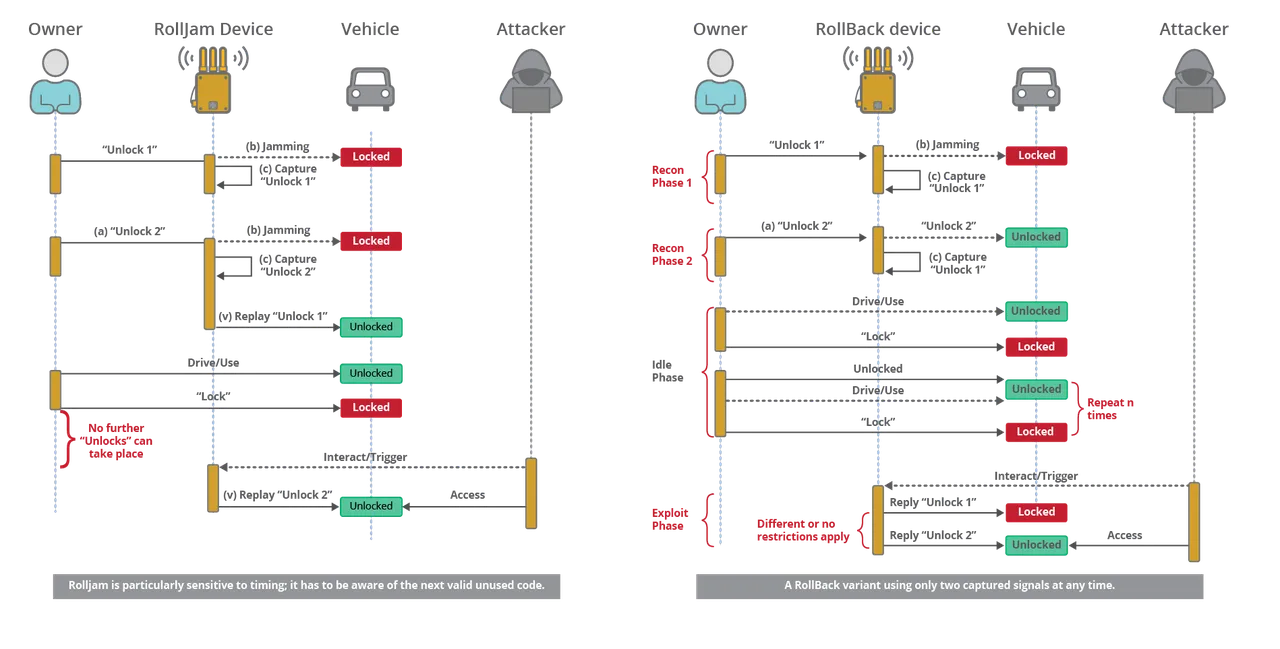
Keyless entry systems have changed how people use car keys and access secure areas, replacing old physical keys with key fobs. However, these systems are vulnerable to RF attacks. Car key fobs use RF signals to send a code to vehicles, allowing them to be unlocked or even started. From the late 1980s to early 2000s, keyless entry systems emerged as a premium on a lot of cars. Like a garage door opener, a button would be pressed on the keyless entry device, transmitting an RF signal to the car, and a code would allow the car to be locked or unlocked. With little-to-no security included in their initial design, early keyless entry systems were vulnerable to cloning and replay attacks. As the technology became more abundant, security increased, adding basic encryption to keyless entry devices and features such as the rolling key method. In the rolling key method, a new code is generated each time a button is pressed on the key fob. With the introduction of rolling keys, basic replay attacks no longer worked because the captured and replayed code didn’t match the newly generated code.
In response to this stronger defense, two new types of replay attacks emerged, the RollBack attack and the RollJam attack. RollBack captures two signals: when a key is pressed, the first signal is jammed, and the second signal is allowed. The first signal is then replayed, and then within five seconds, the second signal is replayed to allow access. Like the RollBack attack, the RollJam attack captures two signals. Unlike RollBack, both signals one and two are jammed, and then signal one is replayed quickly, allowing the owner access to the car. Then the second signal is replayed later by the attacker.
Vehicle theft is a popular use of replay attacks. However, home automation systems can also be victims of these types of attacks. RF doorbell signals can be cloned and replayed, as shown in this demonstration.
Relay Attack
Keyless entry systems are now common features on most cars, and a new premium feature has emerged. With keyless car fobs, a signal from the key fob is always transmitting and the owner does not need to hit a button to unlock the car. Like the replay attack, relay attacks use a device to capture a radio signal. Instead of copying the signal, the device boosts the signal to a second device to make it seem like a key fob is near the car. This attack usually requires two people. The first thief stands close to the car, while the second thief is near the house trying to listen for the always-transmitted signal from the key fob. Once the second thief can get the signal from the key fob, they replay that signal to the first thief. Once the first thief is in the car, the second thief will relay another signal to the first thief, who is now able to start the car.
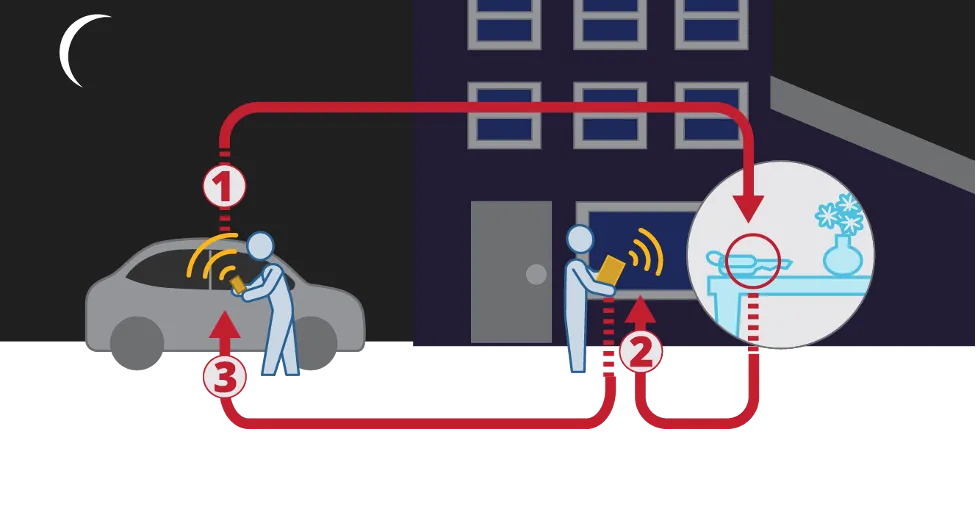
Compounding the issue, all communication signals that use radio frequency must register with the Federal Communication Commission (FCC). Key fobs have an FCC ID, which tells the frequency used. There are commercial tools available that allow an attacker to use the ID to set the frequency on their device, simplifying the process since they do not have to use other tools to scan RF signals and determine the frequency.
Association Flood Attack
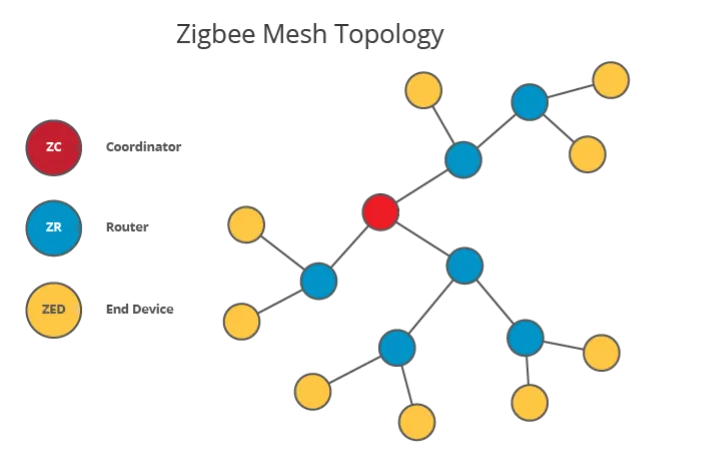
In an association flood attack, an attacker exploits the process by which a new Zigbee node joins a network. In a Zigbee network, there is a coordinator (master of the network), a router, and endpoints. The attack begins when a malicious actor replicates the joining procedures, where a new node sends a beacon request to the coordinator of the network, followed by an association request. By flooding the coordinator with numerous fake requests, the attacker can overwhelm the network. This allows the malicious actor to gain unauthorized access in a network of home or office devices to sensitive data, control devices, or just generally cause disruptions to the Zigbee network.
RF Vulnerabilities in Defense Applications
RF technology is heavily used in defense applications since advanced radio technology is used to carry out operations. Wireless communications have played an integral role in tactical missions and general warfare and defense operations. Secure signals are used to protect voice and data communications during operations. For example, Single Channel Ground and Airborne Radio Systems (SINCGARS) are military systems that provide voice and data to command-and-control operations. There are military-specific GPS signals that are designed to resist jamming and help control the operational environment. Spectrum usage in the military space is a vital part of modern military operations that help support coordination and management. Whether providing voice, data, or mobile ad-hoc networking capabilities to warfighters, RF supports the tracking of equipment or vehicles or coordinating units with aircraft and drones. It is an essential tool for battle planning.
Spoofing and Jamming in GPS and Radar Systems
GPS signals, crucial for navigation and maintaining reliable positioning data for operations, are an essential component of military operations. However, there has been a rise of GPS attacks within the past few years, as these systems can be spoofed or jammed by adversaries. Spoofing involves creating counterfeit signals that can deceive receivers, such as giving an incorrect location. GPS and radar systems are susceptible to association flood attacks, making the entire network believe there are more valid nodes then there really are. The confusion created can be used to mislead drones or unmanned aerial vehicles (UAV) to a wrong destination.
GPS spoofing in military operations is conceptually similar to the car key fob attack described above. In a GPS spoofing attack, an adversary might use ground-based systems to broadcast false GPS signals that deceive military GPS receivers, leading them to navigate to incorrect coordinates. Just as a car can be tricked into accepting a replayed key fob signal, military systems relying on GPS can be misled by a replayed or fake signal. Similarly, an adversary could use an RF jamming device to interfere with a radar system, preventing it from detecting incoming aircraft and misleading radar operators into thinking an incoming aircraft is coming from a different location.
In these cases, the vulnerability lies in the transmission of RF signals without proper safeguards against interception, replay, or manipulation. Further research into safeguarding and securing these systems against risks with more anti-jamming techniques, advanced encryptions, or other pathways will help ensure national security.
Work with the SEI
Understanding RF vulnerabilities and risks is the first step in learning how to mitigate them. Here at the SEI, we are developing tools and processes to securely harness the power of RF. For example, we are developing machine learning (ML) techniques to predict RF signal strength and modulation types to help accelerate the capability of traditional physics-based modeling and simulation. This increased speed can enable applications currently not feasible, such as large-scale risk assessment with uncertainty quantification, design optimization over very large decision spaces, and more realistic real-time war-gaming.
Additionally, the SEI is working to modernize existing processes, data, and digital infrastructure by developing software tools and data pipelines that support RF spectrum operations as the disciplines of wireless communications and traditional cybersecurity operations continue to move towards convergence. If you are interested in learning more about this work or collaborating with the SEI, please contact us.
PUBLISHED IN
Cyber-Physical SystemsGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


