Tactical Cloudlets: Bringing the Cloud to the Tactical Edge
Created March 2022
Making cloud computing resources available to military personnel and first responders in the field presents accessibility and security challenges. Tactical cloudlets provide secure, reliable, and timely access to cloud resources to help military and emergency personnel carry out their mission at the tactical edge despite unreliable connectivity to the cloud.
The Power—and Challenges—of Tactical Cloud Computing
The Department of Defense (DoD) and emergency response agencies have increasingly leveraged mobile devices and cloud-based software applications to perform tasks that support their missions, including speech and image recognition, language translation, and situational awareness.
These missions often take place in hostile “tactical edge” environments with
- limited computing resources
- rapidly changing mission requirements
- high levels of stress
- unstable connectivity
- limited battery power
- limited technical skills in the field
- security vulnerabilities due to limited infrastructure and hostile action (e.g., cyber attacks)
Providing secure, reliable, and flexible computing resources in these environments means that there is a need to “carve out” a piece of the cloud to make it accessible at the tactical edge in a secure, reliable, and timely manner.
How Tactical Cloudlets Support Missions
The SEI has developed “tactical cloudlets,” which are forward-deployed, discoverable computing nodes that can be hosted on vehicles or other platforms to support missions by providing
- extended computing power. Computation-intensive applications and large data sets that exceed computation and storage capability on mobile devices can be hosted on nearby cloudlets.
- forward data staging. Data sets needed for a mission can be pre-loaded on cloudlets to support disconnected operations (i.e., cloudlets disconnected from the enterprise).
- data filtering and formatting. Cloudlets can remove unnecessary data from streams intended for dismounted warfighters to deal with reduced bandwidth and human attention or reformat data to address physical limitations of mobile devices such as reduced screen size.
- data staging. Cloudlets can serve as collection points for data collected in the field from sensors and human input. Data is then uploaded to enterprise repositories as connectivity and bandwidth become available.
- secure credential generation and exchange. Stable connectivity to a centralized credential validation capability in the cloud is not needed to ensure that only authorized personnel have access to cloudlets deployed in the field.
The following diagram illustrates an example of how tactical cloudlets can be deployed in the field to connect personnel to computing capabilities and data sources.
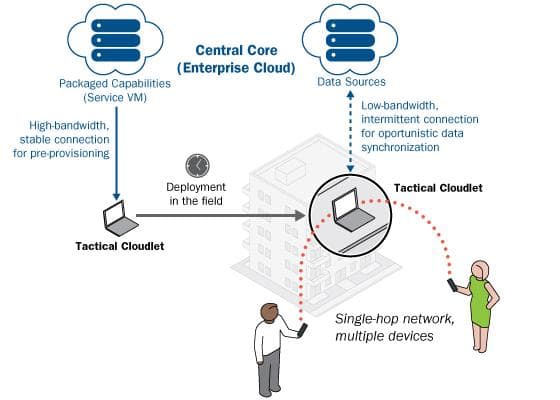
While connected to the cloud, cloudlets are loaded with the capabilities that are needed for a mission. After deployment in the field, users can securely connect to the cloudlet to access those capabilities without the need to be connected to the cloud. For some capabilities, the cloudlet may need to reach back to the cloud when connectivity becomes available, particularly for data synchronization.
Software and Tools
KD-Cloudlet
August 2015
Cloudlets are discoverable, generic, stateless servers located in single-hop proximity of mobile devices that can operate in disconnected mode and are virtual-machine...
readLooking Ahead
Our work to refine tactical cloudlets continues as technologies change.
Because tactical cloudlets are meant to be reusable, they need to have authority to operate (ATO) every time they are reprovisioned. One focus area for future efforts is to automate the cloudlet provisioning process and make cloudlets ready for ATO to reduce operational time and effort.
Our future efforts also involve
- including network configuration for the cloudlet in the process so that it is mission ready and ATO ready
- exploring solutions to improve establishing trusted identities in disconnected environments
- integrating solutions for opportunistic data synchronization with the cloud
We are seeking collaborators to extend this work. We also want to hear about users’ experiences with tactical cloudlets. If interested, please contact us.
Learn More
Engineering of Edge Software Systems: A Report from the November 2022 SEI Workshop on Software Systems at the Edge
June 30, 2023 White Paper
Grace Lewis, Ipek Ozkaya, Kevin A. Pitstick
Based on a workshop with thought leaders in the field, this report identifies recommended areas of focus for engineering software systems at the...
readMoving Cloud Computing to the Tactical Edge
March 26, 2019 Video
Grace Lewis
This video gives a shot snapshot of "Moving Cloud Computing to the Tactical...
watchWhat are the challenges in bringing cloud computing to edge environments?
February 12, 2018 Video
Grace Lewis
Watch Grace Lewis discuss "What are the challenges in bringing cloud computing to edge...
watchSecure VM Migration in Tactical Cloudlets
December 11, 2017 Conference Paper
Grace Lewis, Sebastián Echeverría, Dan J. Klinedinst, Keegan M. Williams
The goal of this paper is to present a solution for secure VM migration between tactical cloudlets based on secure key generation and exchange in the...
readDelay-Tolerant Data Sharing in Tactical Environments
October 02, 2017 Conference Paper
Sebastián Echeverría, Grace Lewis, Marc Novakouski, Jeff Boleng
In this paper we propose a solution for delay-tolerant data sharing, in particular file sharing, using well supported, common networking...
readSEI Cyber Minute: Tactical Cloudlets
March 09, 2017 Video
Grace Lewis
Grace Lewis discusses technical cloudlets and their benefits in...
watchEstablishing Trust in Disconnected Environments
February 26, 2017 Blog Post
Grace Lewis
This SEI Blog post explores techniques for establishing and maintaining trust in disconnected or intermittent network...
readEstablishing Trusted Identities in Disconnected Edge Environments
December 08, 2016 Conference Paper
Sebastián Echeverría, Dan J. Klinedinst, Keegan M. Williams, Grace Lewis
The goal of this paper is to present a solution for establishing trusted identities in disconnected environments based on secure key generation and exchange in the...
read